mirror of
https://codeberg.org/davrot/forgejo.git
synced 2025-07-12 22:00:02 +02:00
Improve template system and panic recovery (#24461)
Partially for #24457 Major changes: 1. The old `signedUserNameStringPointerKey` is quite hacky, use `ctx.Data[SignedUser]` instead 2. Move duplicate code from `Contexter` to `CommonTemplateContextData` 3. Remove incorrect copying&pasting code `ctx.Data["Err_Password"] = true` in API handlers 4. Use one unique `RenderPanicErrorPage` for panic error page rendering 5. Move `stripSlashesMiddleware` to be the first middleware 6. Install global panic recovery handler, it works for both `install` and `web` 7. Make `500.tmpl` only depend minimal template functions/variables, avoid triggering new panics Screenshot: <details> 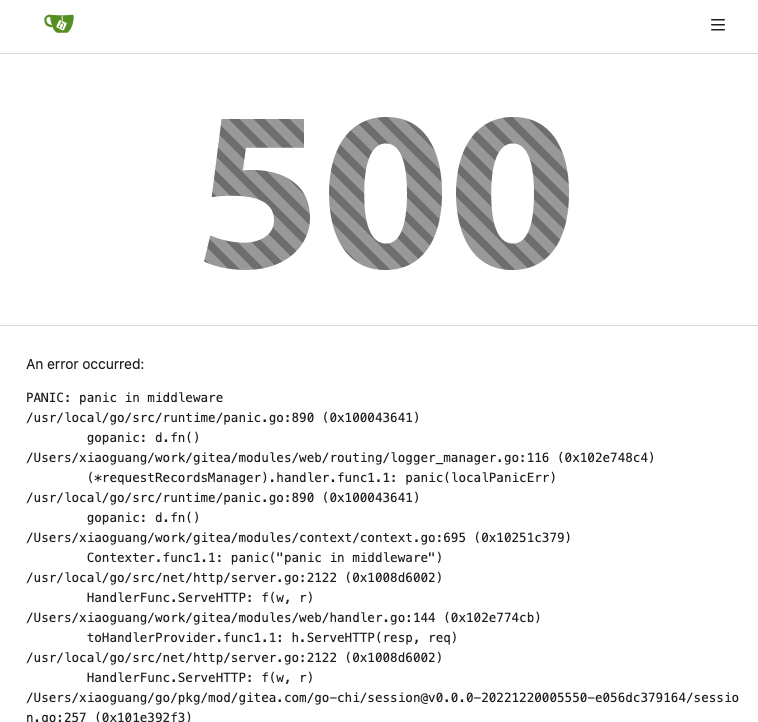 </details>
This commit is contained in:
parent
75ea0d5dba
commit
5d77691d42
25 changed files with 277 additions and 364 deletions
|
|
@ -5,7 +5,6 @@ package context
|
|||
|
||||
import (
|
||||
"bytes"
|
||||
"context"
|
||||
"fmt"
|
||||
"net"
|
||||
"net/http"
|
||||
|
|
@ -13,8 +12,10 @@ import (
|
|||
"text/template"
|
||||
"time"
|
||||
|
||||
user_model "code.gitea.io/gitea/models/user"
|
||||
"code.gitea.io/gitea/modules/log"
|
||||
"code.gitea.io/gitea/modules/setting"
|
||||
"code.gitea.io/gitea/modules/web/middleware"
|
||||
)
|
||||
|
||||
type routerLoggerOptions struct {
|
||||
|
|
@ -26,8 +27,6 @@ type routerLoggerOptions struct {
|
|||
RequestID *string
|
||||
}
|
||||
|
||||
var signedUserNameStringPointerKey interface{} = "signedUserNameStringPointerKey"
|
||||
|
||||
const keyOfRequestIDInTemplate = ".RequestID"
|
||||
|
||||
// According to:
|
||||
|
|
@ -60,8 +59,6 @@ func AccessLogger() func(http.Handler) http.Handler {
|
|||
return func(next http.Handler) http.Handler {
|
||||
return http.HandlerFunc(func(w http.ResponseWriter, req *http.Request) {
|
||||
start := time.Now()
|
||||
identity := "-"
|
||||
r := req.WithContext(context.WithValue(req.Context(), signedUserNameStringPointerKey, &identity))
|
||||
|
||||
var requestID string
|
||||
if needRequestID {
|
||||
|
|
@ -73,9 +70,14 @@ func AccessLogger() func(http.Handler) http.Handler {
|
|||
reqHost = req.RemoteAddr
|
||||
}
|
||||
|
||||
next.ServeHTTP(w, r)
|
||||
next.ServeHTTP(w, req)
|
||||
rw := w.(ResponseWriter)
|
||||
|
||||
identity := "-"
|
||||
data := middleware.GetContextData(req.Context())
|
||||
if signedUser, ok := data[middleware.ContextDataKeySignedUser].(*user_model.User); ok {
|
||||
identity = signedUser.Name
|
||||
}
|
||||
buf := bytes.NewBuffer([]byte{})
|
||||
err = logTemplate.Execute(buf, routerLoggerOptions{
|
||||
req: req,
|
||||
|
|
|
|||
Loading…
Add table
Add a link
Reference in a new issue